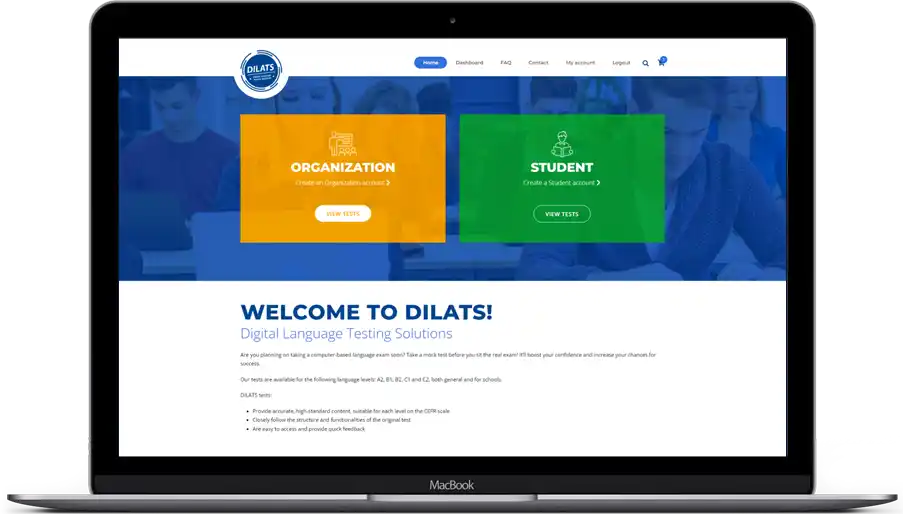
Because practicing the exam should feel like the exam. Dilats bridges the gap between study and simulation. Many learners know the material but stumble when faced with the unfamiliar format...
Developers face a constant challenge: writing clean, maintainable code while keeping up with rapid development demands. Striking the right balance between best practices and long-term sustainability is key to building...
...it is not only about coding, but it is also about being aware of the bigger picture and the needs of the project. Being aware of each step the project...
3 - 5 years experience in PHP, 2+ years experience in Symfony/Laravel framework. Strong OOP knowledge and Design patterns. Extensive work experience with a relational database. RESTful Web Services. Git,...
Job Description This is chance for a QA Engineer with a passion for quality, continuous integration and performance, to work on a long term - high profile project. You will...
Visual content is not to be considered the future of content marketing...it’s here now. Pinterest became one of the top social media channels for visual content. More and more studies...
WordPress 4.8.3 is now available. This is a security release for all previous versions and you are strongly encouraged you to update your websites immediately. WordPress versions 4.8.2 and earlier...
Job Description This is a chance for a Mid Backend PHP developer to work on some of the latest frameworks for high profile projects/clients. Responsibilities will include working in a...
Job Description This is a chance for a Mid Front-End JavaScript developer to work on some of the latest interactive technology for high profile projects. Responsibilities will include implementing visual elements...
Version 4.6 of WordPress was named “Pepper” in honor of jazz baritone saxophonist Park Frederick “Pepper” Adams III. WordPress 4.6 “Pepper” features include: Streamlined Updates You can stay on the...
Web design and development is a collaborative process and it needs your client's involvement in all stages. Learning what your potential clients wants in a website takes time and client...
iOS 9.3 has been in beta since January, and it adds a number of new features to the iPhone and the iPad. One of the biggest user-facing features is Night Shift,...